The update to 5.9 made no indication what drastic changes it was going to do… IT basically broke a working setup.
I fiddled with a bunch of things - all pointing at this symptom :
the pi-hole RPi was only listening on #53 (DNS port) on localhost…
e.g.
this worked (on the Pi)
nslookup google.com 0
(with “0” being common shorthand for localhost)
but not this
nslookup google.com IP.ADDRESS.OF.PI
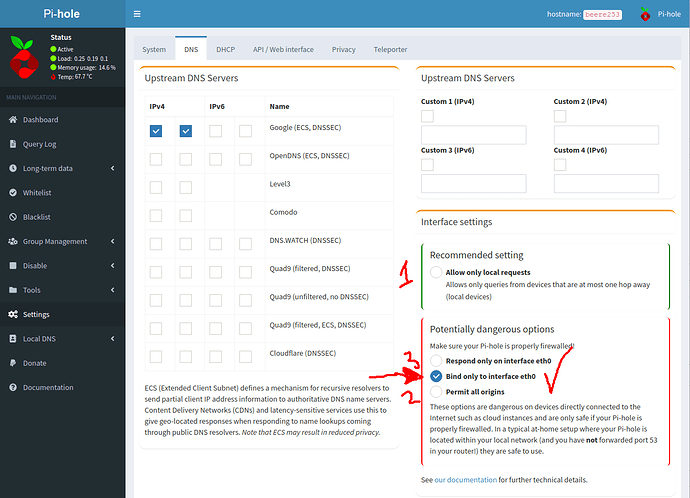
Played with a bunch checkboxes and settings in the considerably changed Admin Web UI :
Tried 1, 2 and 3 and was about to throw in the towel (after wasting time in the terminal looking in things like /etc/dnsmasq.d/ etc - so just before I gave up - I checked “Bind only to interface eth0” and it started working - but - ALL of those other options should have worked. “Permit all origins” should have worked!
╭─x@titan ~/Pictures
╰─➤ nslookup google.com IP.ADDRESS.OF.PI
Server: IP.ADDRESS.OF.PI
Address: IP.ADDRESS.OF.PI#53
Non-authoritative answer:
Name: google.com
Address: 142.250.70.174
Name: google.com
Address: 2404:6800:4015:801::200e
Anyway it’s fixed for now, until the next update breaks everything again?
Not game to use it as my LAN DHCP server (I setup DNS to manual on my NIC settings in Ubuntu).