Hi all, ![]()
I need your opinion on the correct usage of oathtool. In fact it might not be the correct tool for tackling my problem. I have no idea. ![]()
Here´s the background to it all:
Recently I needed to create a personal account for accessing the mail correspondence of my building insurance.
They sent me an activation code by snail mail, which I entered and thus activated my account. So far so good. But now the real trouble starts:
They also sent me some additional information regarding 2FA (2 factor authentication).
This is the rough translation (by trans shell) of the original text:
In order to open specially protected documents, you need a second confirmation in addition to registering in the online mailbox.
To do this you need a so-called “Authenticator APP”.How to open encrypted documents:
To open encrypted documents in your online mailbox, you must register your mailbox in the Authenticator app.
You can use the “Google Authenticator” for your desktop PC.1. How to connect the online mailbox with an authenticator app:
Open the Authenticator app and add a new account.
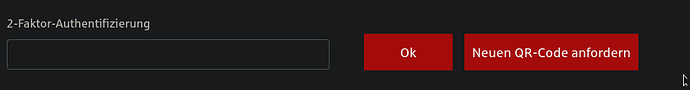
To do this, scan your personal QR code. Alternatively, enter the code: “XXXXXX…”. (32 numbers and letters)A password will then be displayed in your authenticator app. You must enter this password as soon as you log in your online account.
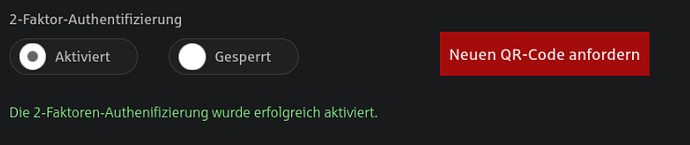
Once you have entered it, your app is permanently connected to the online mailbox.2. How to open encrypted documents in your online mailbox:
Enter the password from your app when prompted. The document opens."
Well, I cannot make head or tail of it… ![]() .
.
I know I can install the Google Authenticator app in Linux (libpam-google-authenticator), but I want to avoid installing anything Google-related if at all possible.
I installed oathtool though.
But I don´t know whether this is good enough for my purposes. ![]()
To try it it out I entered the 32-character-code they provided:
oathtool -b --totp [personal code] and I got a 6-digit password (6 ciphers).
That´s a one-time password, if I understand it correctly, and every time I invoke the command I get a different password, of course.
How is that supposed to work with the 2FA required by my insurance ![]()
Do I need the Google Authenticator App after all?
Thanks a lot for your help in advance.
Many greetings from Rosika ![]()