Hello everyone, unfortunately in recent years I have completely lost faith in everything called “BIG”: Big Pharma, BIG company tech and so on.
I am writing to you because I would like to install a mail server.
I have for the past few years a premiun account in ProtonMail which, among many, I consider the most secure in privacy, but, unfortunately i don’t trust them 100% ;).
I used Virtualmin for some month too, but again, my “obsession” for privacy made me opt for a personal server managed entirely by me.
I use the pc for almost everything: online trading, poker, bill payments and so on, so I need the “maximum” security possible.
What I am asking for is a good firewall configuration that will make me as “secure” as possible.
The only thing I will use the server is for receiving e-mail, nothing else.
I am practicing with the Iptables firewall, but this is all new to me. Searching online, I put together this configuration:
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT DROP [0:0]
:LOGGING - [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG NONE -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN FIN,SYN -j DROP
-A INPUT -p tcp -m tcp --tcp-flags SYN,RST SYN,RST -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,ACK,URG -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,RST FIN,RST -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,ACK FIN -j DROP
-A INPUT -p tcp -m tcp --tcp-flags PSH,ACK PSH -j DROP
-A INPUT -p tcp -m tcp --tcp-flags ACK,URG URG -j DROP
-A INPUT -i enp5s0 -p tcp -m state --state NEW -m recent --set --name DEFAULT --mask 255.255.255.255 --rsource
-A INPUT -i enp5s0 -p tcp -m state --state NEW -m recent --update --seconds 30 --hitcount 10 --name DEFAULT --mask 255.255.255.255 --rsource -j DROP
-A INPUT -j LOGGING
-A INPUT -p icmp -m length --length 200:65535 -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,PSH,URG -j DROP
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,PSH,ACK,URG -j DROP
-A INPUT -p icmp -m icmp --icmp-type 13 -j DROP
-A FORWARD -i enp5s0 -p tcp -m state --state NEW -m recent --set --name DEFAULT --mask 255.255.255.255 --rsource
-A FORWARD -i enp5s0 -p tcp -m state --state NEW -m recent --update --seconds 30 --hitcount 10 --name DEFAULT --mask 255.255.255.255 --rsource -j DROP
-A OUTPUT -p tcp -m tcp --dport 53 -j ACCEPT
-A OUTPUT -p udp -m udp --dport 53 -j ACCEPT
-A OUTPUT -p tcp -m tcp --dport 80 -j ACCEPT
-A OUTPUT -p tcp -m tcp --dport 443 -j ACCEPT
-A OUTPUT -p icmp -m icmp --icmp-type 14 -j DROP
-A LOGGING -m limit --limit 5/min -j LOG --log-prefix "IPTables denied: " --log-level 7
-A LOGGING -j DROP
COMMIT
I use Postfix as my SMTP server and i have an dedicated IP.
P.s. hopefully you understand my bas english ![]()
You may find ufw a lot easier than iptables
I wonder whether in putting a mail server on the internet, you are going to
jeopardize your security more than you would by staying behind NAT and
using a normal email client. You can encrypt emails.
Postfix can’t do that for you.
I’ve had good luck with a mail server called SmarterMail. It runs on Windows, but they just rolled out a Linux version. Maybe it’s still in beta, but it looks very nice and includes email, calendar, contacts, tasks, and more. It has built-in antispam and antivirus.
SmarterMail Business Email and Collaboration Server (smartertools.com)
They have a free version you can use forever as long as you use one domain and fewer than 10 email addresses. Not sure of the limits.
Maybe I explained myself wrongly… I do NOT want to download the emails to their servers. Going to install my own server opens some ports: SMTP and IMAP. By opening these two ports do I still remain “safe”?
Regarding the configuration of Iptables, what is wrong with protecting against porst scanner, flood, invalid packets, ICMP requests, etc etc?
“by staying behind NAT” is this NAT config site in my router?
I mean SMTP ![]()
Every port you open decreases safety.
[quote=“lol, post:5, topic:12106, username:lol”]
“by staying behind NAT” is this NAT config site in my router?
[/quote].
Your PC probably has masquerading configured by default.
I think the router will have it too.
You will also have to have a full DNS “MX” record before relays will send to your hosted solution… I don’t know if there are any “free” MX DNS record services… Never even tried this myself with Dynamic DNS (i.e. 95% of users with ISP’s don’t get a fixed IP address), DNS MX records usually go to FIXED ip addresses - but I guess it could work with something like dyndns or NoIP (pretty sure I can get an MX DNS record with my NoIP plan [paid for - but expires soon] - but I don’t think NoIP’s free plans can have MX records) .
Yes it is.
However, you need to expose the needed ports via port forwarding.
Yes, and no.
Opening a port is an abstract thing, which basically means there’s a service that listens on that port and answers requests.
If you configure postfix the right way, you will be kind of safe, despite SMTP ports being open. You could close those ports via a firewall despite postfix running, but doing so you will loose the functionality of postfix.
If you create an open relay by accident (misconfigure postfix) you are asking for trouble.
The same applies to dovecot/courier and IMAP ports ![]()
Beware that bad guys are going to hammer your postfix instance even if it is well configured, once you have it online and running.
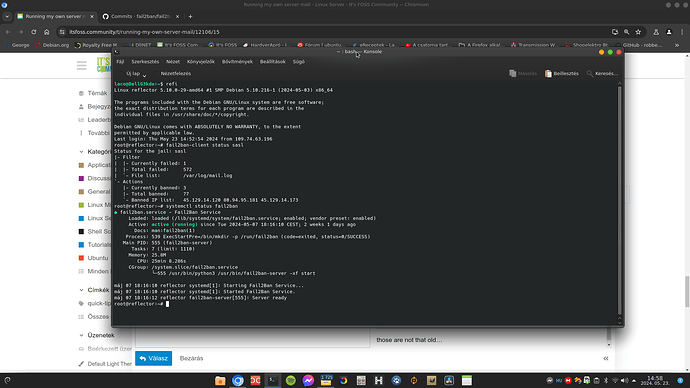
Fail2ban is good way to keep them away.
Since a couple years I run my servers which includes email too.
On my servers I have Fail2ban.
SMTP is definietly the most popular target for attackers.
The silver medalist is the ssh port.
You’ll find lots of tutorials how to set up properly a self hosted mailserver.
Dynu.com allows it.
Well, not for a fresh registration, but after 30 day passed, it allows all kinds of DNS records.
It is a dyn-dns like service, so yes, it works for dynamicIP…
Yes, running my own server for some days, everythig is already setup where i bought my domain name. ![]()
Thanks László Kovács, for explanation, yup i know about Fail2ban, but i noticed is not supported for several years, is still good?
A question: in case I decide to do this, would you be willing to give me some suggestions? ![]()
Then a port fowarding is needed ![]() I’m still thinking about… not sure i’ll take this risk, but having an own server running is king, i really like this idea…
I’m still thinking about… not sure i’ll take this risk, but having an own server running is king, i really like this idea…
???
It’s in the Debian repo.
GitHub - fail2ban/fail2ban: Daemon to ban hosts that cause multiple authentication errors my wrong, sometimes ago i read it wasn’t updated for several years.
The safe way to experiment is to dedicate a spare machine to it, and isolate it from the rest of your home network.
Then you can make all the mistakes required to learn, and no damage will result.
I use Fail2ban on my Debian powered servers
I don’t know aft nor dd-dreams.
If you look at commits of Fail2ban itself:
those are not that old…
And as it’s already packaged by Debian, I just use it, and it kinda works ![]()
Well, if it’s about a mail server, it can cause a HUUGE damage.
Namely, the reputation of the domain name will be disrupted.
If spammers get access to send out the junk, they probably will do it in mass.
The domain name quickly gets blakclisted, and it will be impossible to get legitim mails delivered.
Won’t work without opening/exposing ports ![]()
My best advice is to look at tutorials, but don’t follow them blindly.
Consult postfix manual, do understand what is done in the configs in the choosen tutorial.