Hi all, ![]()
Lately I stumbled across an article which made me ponder about the aspect of security with regards to ubuntu vs debian.
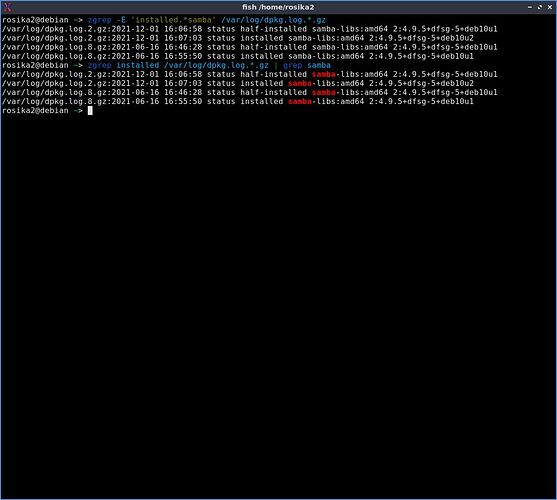
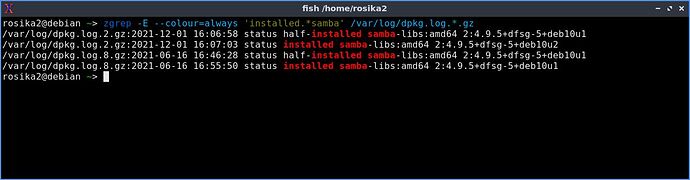
Currently I´m using Debian Buster (stable) in a VM, so in this scenario might not be of really great relevance for me but for those using Debian stable as their daily driver it´s certainly something else. ![]()
The article I´m referring to can be found here:
Sicherheitsupdates bei Debian – Wie viel Verzögerung ist normal? | [Mer]Curius .
Alas it´s written in German, so I´ll try to summarize it (to a certain degree) here.
rough translation:
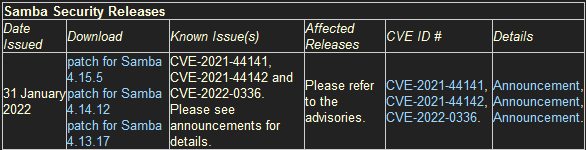
During the last few days, a gap in Samba has hit the newspapers.
This is a replica of Windows network services that almost every Linux distribution has preinstalled.
The problem is in the vfs_fruit module.
Apple users are probably familiar with this as a prerequisite for storing Time Machine backups on a Linux server.The vulnerability is classified as critical and registered under CVE-2021-44142.
All distributions I know of quickly rolled out patches. Ubuntu, SUSE, Red Hat - the patches were usually already on my system before I read the corresponding message. Only with Debian nothing has happened for days - again.
Chromium is also lagging behind once more and when skimming over the current security issues, I immediately noticed a few packages for which I have had updates on my openSUSE Leap systems for days (e.g. Expat), although to be fair they are not particularly critical.
The same with MariaDB […]
Two points just surprise me:
1.) How did Debian get its reputation as a secure operating system? They offer average at best when looking at the speed of response to issues.
2.) Why doesn’t anyone in the Debian community notice this at all? I haven’t found a single serious discussion about it.
For example, one could discuss how high the price one is willing to pay can be to keep versions absolutely stable.
Which packages do you want to sacrifice for this, how much delay in security updates do you find acceptable for this goal?
Do you prioritize things like reproducible builds over security? Those would be interesting points for a policy.
(author: [Mer]Curius )
My thoughts about this article were:
Does anyone of you use Debian stable ![]()
And if so, what experience with Debian stable do you have as far as security updates are concerned ![]()
I´m deliberately not speaking of testing or Sid (unstable). My question just refers to stable.
I know its primary goal is (as the name suggests) stability of packages. Absolutely not bleeding edge.
This is exactly what I would be looking for in Debian stable. ![]()
But timely updates of security patches would still be vital methinks. ![]()
Thanks for your opinions in advance.
Many greetings
Rosika ![]()
P.S.:
At the time of writing CVE-2021-44142 still lists “CVE-2021-44142” as vulnerable.
In contrast to that I received security patches on my Lubuntu system as early as Feb 1:
2022-02-01 14:37:56 status installed samba-libs:amd64 2:4.13.17~dfsg-0ubuntu0.21.04.1