Single File Transfers
Notice: For my experiments I was using Linux Lite 6.2 (based on Ubuntu) as host and Archlinux as guest
Using SSH , SCP and SFTP Between Guest and Host:
On Linux Lite (Host System):
Install SSH Client and SSH server:
- Open a terminal on your host system. ( Linux Lite in my case)
- Run the following commands to install the SSH client and SSH server
sudo apt update
sudo apt install openssh-client openssh-server
On Arch Linux (Guest System):
1.Install SSH Server:
- Open a terminal on your guest system (Arch Linux in my case).
- Run the following commands to install the OpenSSH package (which includes the SSH server):
sudo pacman -Syu # to upgrade Arch first
sudo pacman -S openssh
sudo pacman -S fuse3
2.Enable and Start SSH Service:
sudo systemctl enable sshd
sudo systemctl start sshd
3.Check SSH Status:
… to ensure that the SSH service is running
ps ax | grep sshd
or
systemctl status sshd
● ssh.service - OpenBSD Secure Shell server
Loaded: loaded (/lib/systemd/system/ssh.service; enabled; vendor preset: e>
Active: active (running) since Thu 2024-02-29 14:42:22 CET; 2h 24min ago
[...]
Using SSH and SFTP:
- SSH Connection from Guest to Host:
working with the host´s ip address:
-
In your Arch guest system, open a terminal.
-
In case you don´t know it already you have to obtain your host´s ip address first.
You can use command-line tools within the host to retrieve its ip address. For example, you may use commands like ifconfig
or ip addr to display network interface information, including the ip address assigned to your host.
-
example for ifconfig:
enx001e101f0000: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.8.102 netmask 255.255.255.0 broadcast 192.168.8.255
[...]
… indicating the respective ip address is 192.168.8.102.
ip addr
[...]
4: enx001e101f0000: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:1e:10:1f:00:00 brd ff:ff:ff:ff:ff:ff
inet 192.168.8.102/24 brd 192.168.8.255 scope global dynamic noprefixroute enx001e101f0000
… providing the same result.
- Use the following command to connect to your host system via SSH:
ssh username@host_ip_address
Replace username with your username of the host and host_ip_address with the ip address of your host.
example:
arch@archlinux ~> ssh rosika@192.168.8.102
rosika@192.168.8.102's password:
Welcome to Linux Lite 6.2 (GNU/Linux 5.15.0-97-generic x86_64)
[...]
rosika@rosika-Lenovo-H520e ~> whoami
rosika
rosika@rosika-Lenovo-H520e ~> pwd
/home/rosika
rosika@rosika-Lenovo-H520e ~> exit
Connection to 192.168.8.102 closed.
arch@archlinux ~>
working with the host´s hostname:
-
in case you don´t know it already get your host´s hostname: hostname.
In my case the command provides the output “rosika-Lenovo-H520e”.
-
Trying to ssh into the host from the VM for the first time gave me the following information:
“ssh: Could not resolve hostname rosika-lenovo-h520e: Name or service not known”.
So I had to resolve the hostname “rosika-lenovo-h520e” to an ip address first.
This was done by editing the /etc/hosts file.
Open the /etc/hosts file on your VM using a text editor.
Add an entry mapping the hostname “rosika-lenovo-h520e” (your hostname, of course) to the corresponding IP address.
The entry should look like this:
192.168.8.102 rosika-lenovo-h520e
Save the file and exit the text editor.
This is an example using my system. You´d have to provide your own hostname and the correct ip address.
Now ssh-ing into the host works:
ssh rosika@rosika-Lenovo-H520e
The authenticity of host 'rosika-lenovo-h520e (192.168.8.102)' can't be established.
[XXXXXXX] key fingerprint is SHA256:[XXXXXXXXX....].
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:1: 192.168.8.102
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'rosika-lenovo-h520e' [XXXXXXX] to the list of known hosts.
rosika@rosika-lenovo-h520e's password:
Welcome to Linux Lite 6.2 (GNU/Linux 5.15.0-97-generic x86_64)
[...]
Willkommen zu fish, der freundlichen interaktiven Shell
Type help for instructions on how to use fish
rosika@rosika-Lenovo-H520e ~> exit
Connection to rosika-lenovo-h520e closed.
arch@archlinux ~>
Note:
The respective fingerprint has to be added when trying to connect for the first time. This has to be done only once.
When you connect to a remote host for the first time, SSH compares the fingerprint of the remote host’s public key with the one stored in your known_hosts file.
If the fingerprint doesn’t match or if the remote host’s key isn’t in your known_hosts file, SSH prompts you to confirm whether you want to
add the host’s key to the known_hosts file (~/.ssh/known_hosts).
By saying “yes” and adding the fingerprint, you’re acknowledging that you trust the remote host’s identity and want to proceed with the connection.
This is a security step to ensure that you’re connecting to the correct host and not falling victim to a man-in-the-middle attack.
working with the VM´s ip number on boxes virtual net:
It´s also possible to ssh from a virtual machine (VM) running in Gnome Boxes to the host machine using the host’s IP address on the virtual network.
When you’re using gnome-boxes, it creates a virtual network interface on the host machine to facilitate communication between the host and guest VMs.
This virtual network interface typically has its own IP address range separate from the host’s actual network interface.
The host’s IP address on the virtual network is 10.0.2.2, and we should be able to ssh from the guest VM to the host using that ip address.
arch@archlinux ~> ssh rosika@10.0.2.2
The authenticity of host '10.0.2.2 (10.0.2.2)' can't be established.
XXXXXXX key fingerprint is SHA256:[XXXXXXXXX....].
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:1: 192.168.8.102
~/.ssh/known_hosts:5: rosika-lenovo-h520e
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Welcome to Linux Lite 6.2 (GNU/Linux 5.15.0-97-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
[...]
You have mail.
Last login: Fri Mar 1 17:20:47 2024 from 192.168.8.102
Willkommen zu fish, der freundlichen interaktiven Shell
Type help for instructions on how to use fish
rosika@rosika-Lenovo-H520e ~> whoami
rosika
rosika@rosika-Lenovo-H520e ~> exit
Connection to 10.0.2.2 closed.
arch@archlinux ~>
Note: see above
SSH is of limited usefulness. To transfer files one needs to use sftp or scp
- SFTP File Transfer:
To transfer files between your guest and host systems using SFTP, you can use the sftp command in your guest system’s terminal:
sftp username@host_ip_address
This way you can upload and download files securely.
example:
archlinux ~> sftp rosika@192.168.8.102
rosika@192.168.8.102's password:
Connected to 192.168.8.102.
sftp> help
Available commands:
[...]
get [-afpR] remote [local] Download file
[...]
put [-afpR] local [remote] Upload file
[...]
sftp> bye
arch@archlinux ~>
Note that all of the 3 ways of specifying a host in the ssh command apply also to sftp.
- SCP File Transfer:
scp (secure copy) is a command-line utility that allows users to securely copy files and directories between hosts over an SSH connection.
This is the general syntax: scp [options] source destination.
example:
The aim is to copy a python file from Archlinux (running in gnome-boxes to the Linux Lite host.
arch@archlinux ~> scp /home/arch/Ergänzungen_zu_Programmen/zu_passphrasegen/passphrasegen-script.py rosika@192.168.8.102:/media/rosika/f14a27c2-0b49-4607-94ea-2e56bbf76fe1/DATEN-PARTITION/Dokumente/Ergänzungen_zu_Programmen/zu_passphrasegen/
rosika@192.168.8.102's password:
passphrasegen-script.py 100% 549 101.1KB/s 00:00
arch@archlinux ~>
Notes:
scp encrypts both the file contents and the file metadata during the transfer, thus ensuring data integrity.- It uses SSH for authentication, allowing users to securely transfer files using their SSH credentials.
- The -r option enables recursive copying, allowing users to copy entire directories and their contents in a single command.
Note that all of the 3 ways of specifying a host to the ssh command apply also to scp
Additional Remarks:
We´ve been covering file transfers operated from within the gnome-boxes guest only. The transfers can be in either direction, guest to host or host to guest, but must be controlled from the guest.
The methods described here wouldn´t work the other way round ( ie operated from the host), unlike in virt-manager.
That´s due to the fact that gnome-boxes and virt-manager handle networking differently, which affects how you establish connections between the host and guest systems.
Gnome Boxes typically sets up a NAT (Network Address Translation) network by default for its guests.
This allows the guest systems to access resources on the host and the internet. However, connections from the host
or even from any other machines on the network to the guest are not enabled.
In this setup, the guest system (Arch Linux in my case) obtains an IP address from the internal NAT network,
which may not be directly accessible from the host system.
Virt-manager, however, offers more flexibility in networking configurations. While it can set up NAT networks,
it can also handle various other network configurations, like bridged and host-only networking.
In a bridged network configuration, the guest system obtains an IP address from the same network as the host system,
which should make it accessible from other machines on the network.
Links:
Drag and Drop Files between Host and Guest with Thunar
One of the convenient features of Gnome Boxes is the ability to transfer files between the host and guest operating systems using thunar
in a simple and effective way. Thunar is the default file manager in many Linux distributions, however the procedure should work
with other file managers which support the ssh protocol, like nautilus and konqueror, as well.
-
In the guest open 2 instances of thunar next to each other.
-
In one of them navigate to the address bar and enter the host´s ip address: ssh://username@host_ip_address.
In my case it was: ssh://rosika@192.168.8.102.
Replace username with your host username and host_ip_address with the ip address of your host machine on the virtual network.
-
You will be prompted to authenticate with your host’s password (popup window).

- After successful authentication, the address bar changes to
sftp://username@host_ip_address, indicating a secure FTP connection
to the host’s file system. Thunar now displays the root directory of the host machine, allowing you to browse its contents.
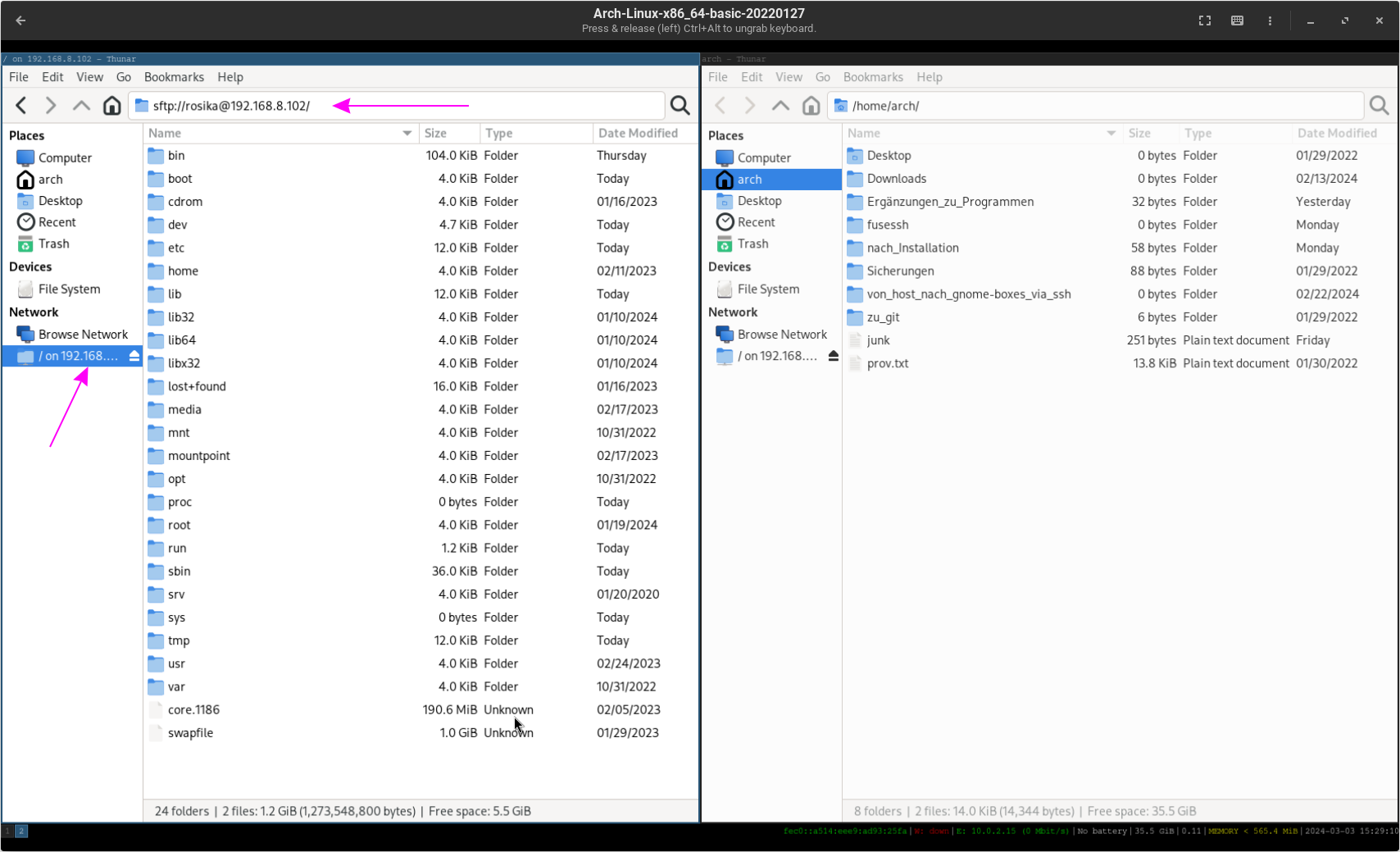
- With
thnunar open to the host’s file system, you can navigate to any directory and locate the files you wish to transfer.
Simply drag the files from the host’s thunar window and drop them into the guest’s thunar window.
The files will be seamlessly transferred from the host to the guest over the secure SSH connection.

-
After you´re done just unmount it from thunar´s network listings.
-
For convenience you may also create a respective bookmark in thunar, so accessing any of the host´s files at a later time
would be much easier.

Benefits:
- Seamless Integration:
thunar’s drag and drop functionality provides a seamless way to transfer files between the host and guest operating systems.
- Security: The use of SSH ensures secure file transfers between the host and guest.
- Convenience: With just a few clicks, you can transfer files without the need for external storage devices or complicated network configurations.