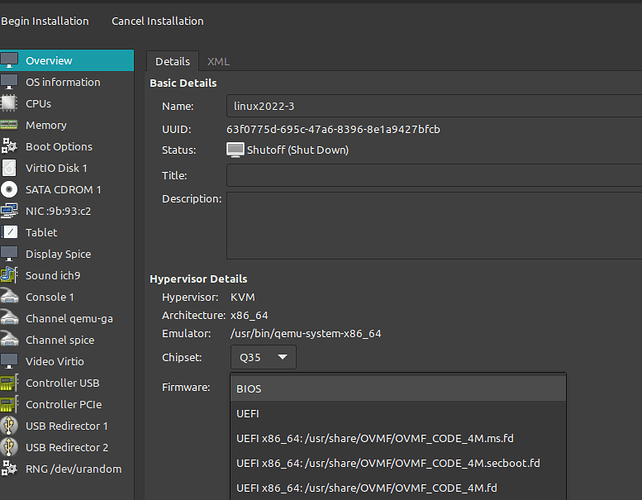
The previous link on the OS2 info has screenshots of the installation process. And the first thing you read is that VOS2 went from an OS based on Ubuntu to a hybrid.
Hybrid Debian Base
The system consists of a hybrid base of Debian packages and Vib modules. The major change in Orchid is the switch from Ubuntu to Debian, providing more flexibility and control over the system and update distribution.
Regarding updates, we transitioned from a package-based structure to an OCI image-based structure, using Vib, a technology developed by us. It allows us to assemble OCI images using modules of various types, such as Debian packages, software builds, scripts, etc. It enables us to provide updates in the exact state they got tested, ensuring every user receives the same updates.
*But I do want to walk through the options I chose and why you may or may not choose those from the start. And one thing that surprised me was something @nevj mentioned in a post about wishing there was a log to view after install of an OS. Well I was offered the option to see the log. The first 50 lines or so were meaningless to me but then it began to show each package installed, etc. *
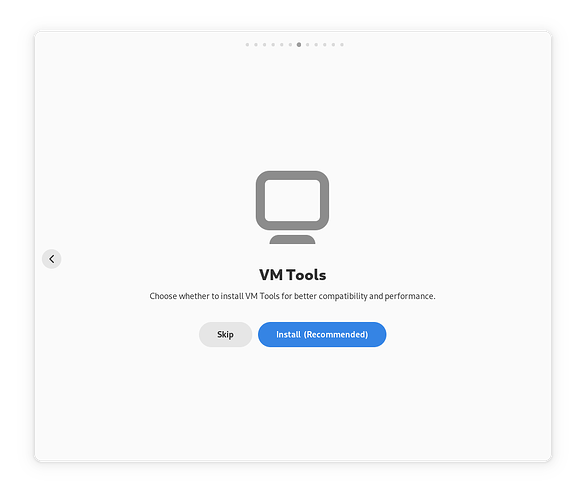
First up, VM tools:
" If you decide to install them, the Installer will use a vm dedicated image, which includes the tools and drivers for the most common virtualization platforms."
I’m not sure, yet, what exactly those tools are composed of, but I will see if it is possible to “test a VM” with them inside a VM.
Besides the normal install options of language, keyboard, etc., there was the option to install apps (office, utilities, etc.) and I chose to do so. As I watched the list of them get installed, I regretted that decision. This OS also uses flatpak as first choice and so all of those apps like LibreOffice got the flatpak version installed. I prefer to install the .deb pkg offered from the sources.
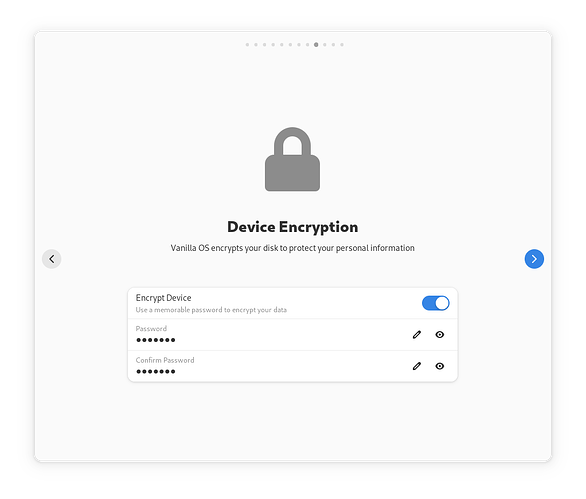
After internet connection was the encryption option:
“You can choose to encrypt the /var partition (partition that holds all user data) with LUKS2 for maximum data security (recommended).”
I skipped this since I will not have any need for it in the VM.
Once I got to the first startup, that is where things differed from my other installs in the past.
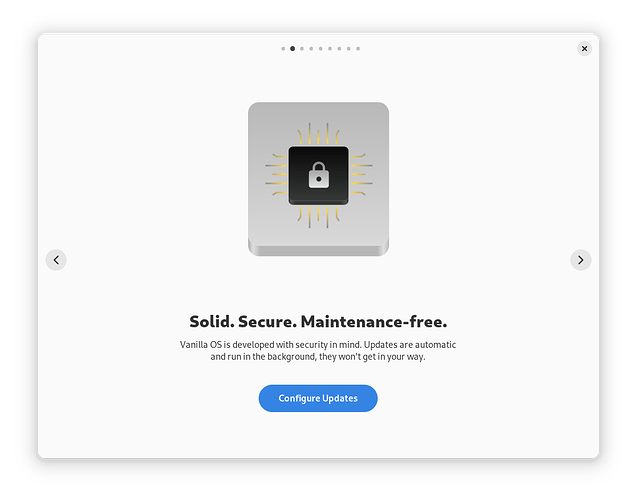
I should have chosen Advanced, but I did not. So from there the first screen introduced Vanilla OS 2 updates info:
That did not sit well with me as I do not just apply updates randomly or at the suggestion of the OS unless I know what is going to be updated/installed. And I prefer the terminal as I like to see what is happening at the time, including any errors.
Configure updates gave me the normal option of not applying their “smart” updates and you can choose the frequency if you do not like being bothered by the normal updater on a daily basis (or more).
The rest of the first start info is pretty standard for setting up your system (i.e., bluetooth devices, introduction to the “store”) as well as some interesting items like the ability to use .deb and .apk files. They claim if your app is only availble on Android, you can install it on Vanilla OS 2.
I will definitely be testing that one out as the last time I tried Waydroid, it required a Wayland session. For me, there are still apps that do not work on Wayland so this could be the answer to that.
There was also something for developers. Which I am most certainly not.
If anyone would like to expound upon that and how it differs from other Linux OS options, I would be interested in hearing about it.
Then you are told that the Super key is used for seeing all open apps (and I expect workspaces, if they are an option, as well):
The next screen was of interest to me, but will not be able to test it in a VM.
PRIME Profiles
With the departure from Ubuntu as the base for the system, we had to rewrite support for switching PRIME profiles, a feature that allows quick and easy switching between graphics cards.
Due to the complexities of porting this feature to Vanilla OS 2 and its unique immutable structure, we developed a new tool (prime-switch) compatible with the new system.
prime-switch is a command-line tool, but we simplified its usage by integrating a new screen in Settings, under the Display section, allowing users to change the PRIME profile easily without resorting to the command line.
Following are some of the things that differ in this OS from other Linux distributions.
ABRoot v2
ABRoot, our implementation of A/B Partitioning, facilitates updates in an immutable system through atomic transactions between two partitions, ensuring a consistently functioning system.
In Vanilla OS 2 Orchid, we introduced ABRoot v2, a complete rewrite of the project designed to be more reliable and faster. Transactions now occur through OCI image expansion instead of applying package updates, ensuring the system receives an exact copy of the tested image.
ABRoot v2 brings additional features, such as the ability to dump the system state for support in case of issues, switching between flavors without data loss by changing the base image, auto-recovery of the ABRoot file system structure, and more.
Driver and System Changes
In ABRoot v1, users could access the transactional shell to make atomic system changes. In ABRoot v2, this feature was removed, and replaced by support for generating custom local images. For example, when installing a driver not present in the system, ABRoot can generate a custom image with the driver installed, similar to a traditional package manager but creating a local OCI image used for updates. While this feature was introduced out of necessity, it is not recommended for daily use and should only be used for driver installations, as it puts the system in an indeterminate state.
To minimize the need for this operation, Vanilla OS now includes a broad set of drivers, covering most peripherals. In some cases, multiple OCI images were created to cover different scenarios (i.e. NVIDIA, VM). During installation, Vanilla OS proposes the most suitable image based on detected hardware.
LVM Thin Provisioning
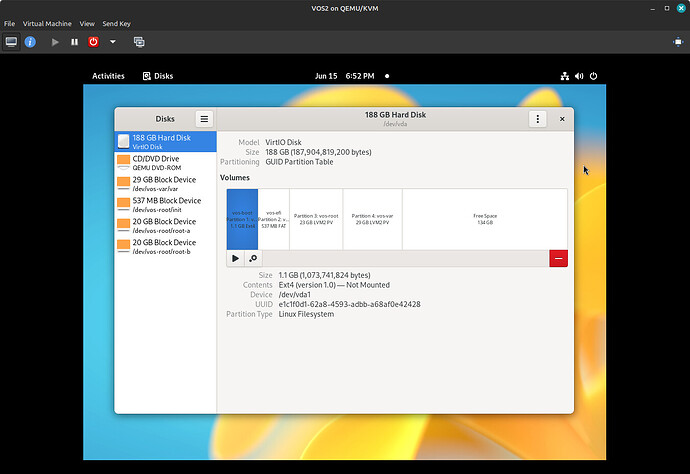
Addressing a major criticism of Vanilla OS 22.10, which was the allocated space for the two root partitions, totalling 20GB for root and taking up 40GB of disk space, we introduced support for LVM Thin Provisioning.
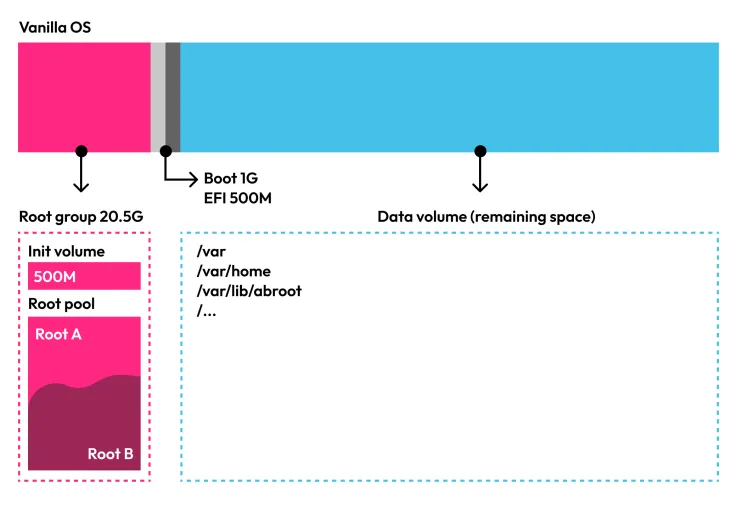
This technology allows the creation of logical volumes with variable sizes, optimizing disk space usage. Now, the two root partitions share a total of 20GB, dynamically allocated based on the size of the two partitions, providing more disk space for user data.
Sudon’t
Having sudo is a common practice in Linux, but it is not secure. In Vanilla OS 2 Orchid, we have replaced sudo with PolKit policies, allowing users to perform privileged operations in a more controlled and secure manner.
PolKit, unlike sudo, is integrated into the system as a centralized authentication authority and privileged operations are managed through specific policies defined for each action. This structure provides greater control and prevents users from inadvertently or intentionally running malicious scripts that could compromise the system. Normally, such scripts would use sudo to execute privileged operations, and even if adapted to use the counterpart pkexec, they can’t be executed without the safer graphical interaction of the user.
The user will still have access to sudo but within the VSO subsystem.
I hope I am interpreting that incorrectly as it sounds to me like the OS does not trust me to manage my own system with sudo and is making it more difficult to use that in CLI and instead, I will have to use the GUI to ensure I do not “inadvertently run malicious scripts” or otherwise “compromise my system.” That sounds very Windows-esque, for lack of a better term. You know, the “Windows kept you from harming your system” popup you get when you try to install an app you want and MS does not want you to use? 
I was not aware of the previous criticism of 2 root partitions in the setup of VOS1, so I guess for those who will be transitioning, this LVM Thin Provisioning is a plus.
Vanilla System Operator and Apx
VSO (Vanilla System Operator) and Apx are familiar tools for Vanilla OS users. In Vanilla OS 2, both tools underwent significant rewriting to cover various scenarios.
VSO v2
VSO v2 is no longer just an update manager but also serves as the system shell, and package manager, and provides support for Android applications. In Vanilla OS 2, users no longer have direct access to the system shell; opening the console brings them to the VSO shell, an integrated and mutable Vanilla OS subsystem. It allows users to install and run applications as they would in any Linux distribution without affecting the system.
Additionally, VSO now supports Android applications, which can be installed and run as native applications without the need for an emulator. The Android subsystem is isolated from the system and can be initialized at the user’s discretion.
To simplify the experience, we integrated the F-Droid store into VSO, allowing users to install Android applications without relying on external sources.
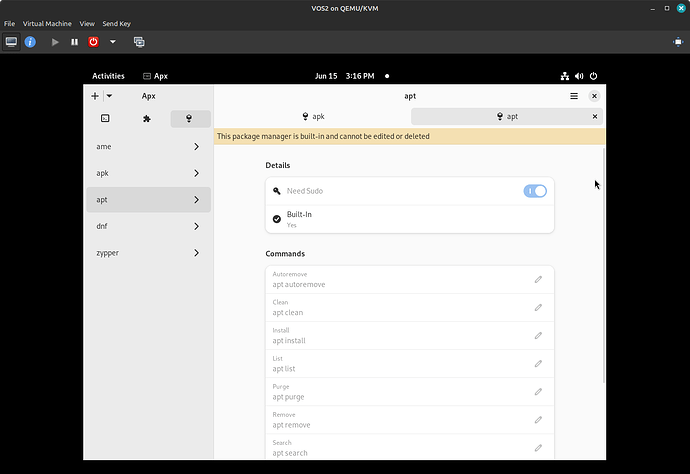
So if VSO v2 is the “package manager” does that mean “sudo apt update” no longer works? Aside from “sudo” not working, that is.
I did not see the normal terminal icon on the dock in the Gnome desktop so I searched “terminal” and Black Box came up. Once I clicked on it, it opened a terminal-like black box and proceeded to install what I assum is VOS2’s terminal emulator. “sudo apt update” did, indeed, work. Okay. So far so good.
I will say I was surprised by the Gnome DE. And I did not see any other DEs from the login screen so I will be checking if others are available to install. Of course, being the beta, it may not be an option yet. But if it was available for VOS1, that would indicate their intent to have others available.
Then the further explanation of the subsytems.
DEB/APX Sideloading
Given the enhanced capabilities of VSO, we simplified the way users install unofficial packages. In Vanilla OS 2, users can install .deb and .apk packages by simply opening them with the Sideloading application, which handles the installation into the correct subsystem.
I will test this out further.
Now for the developer portion:
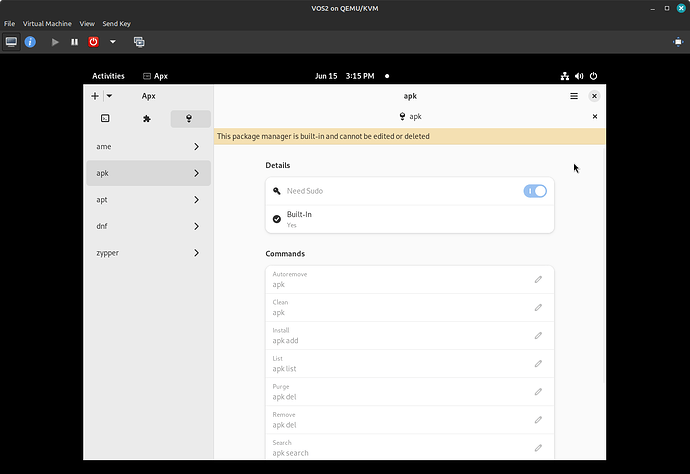
Apx v2
Apx v2 now plays an entirely new role by serving as a powerful tool for developers and creators. It allows the creation of custom environments (stacks) for various needs. While Apx v2 got rewritten from scratch, its usage method remains similar. Users can now create custom stacks, defining which packages to install and creating one or more subsystems based on these stacks.
Despite the rewrite, Apx v2 allows users to create custom stacks and access created subsystems through direct shells or by leveraging the declared package manager in the stack. Users can then export the applications to the main system and more. The only limit is their imagination.
Responding to a common request, Apx v2 supports package managers other than those provided in Apx v1, allowing users to define the package manager to use in a stack. For example, users can create a stack based on Arch Linux, defining yay as the package manager instead of pacman, and install packages from AUR without issues.
Apx GUI
Among the many new features of Apx v2, we introduced a graphical interface, Apx GUI, facilitating the management and access to created subsystems quickly and easily.
I do not have a grub menu since the initial install in VM, but I am assuming this is part of their grub. I did read that installing VOS2 in a dual-boot system is not recommended and I can see why.
FsGuard and FsWarn
One of the goals of Vanilla OS 2 Orchid is to make the system more secure and reliable. To achieve this, we introduced two new tools, FsGuard and FsWarn, developed in collaboration with Linux Immutability Tools.
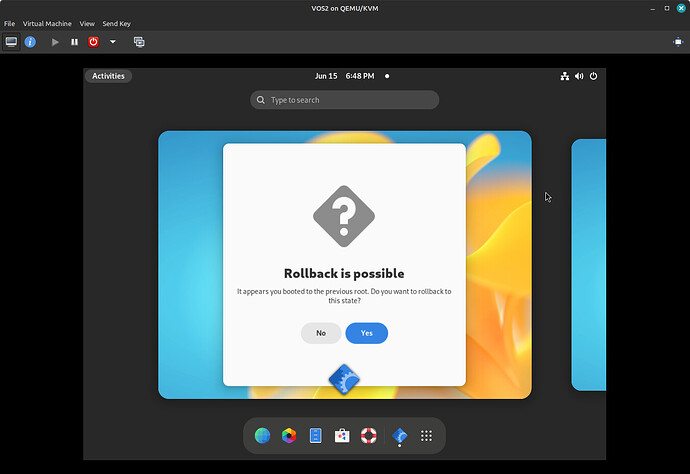
FsGuard is the tool that initiates during the system boot, checking the integrity of the system binaries to ensure no discrepancies with the state provided by the system image. If a modification is detected, FsGuard will start FsWarn, which halts the system boot, notifying the user of the issue and advising them to restart the system to the previous state, ensuring system’s integrity. Users can choose to ignore the warning and start the system, but in this case, we cannot guarantee the system’s integrity and you may encounter serious issues.
The HELP documentation is very basic and I may be mistaken, but it could be due to the OS itself being very basic, at least at this point. There are no forums yet. Hmmm. So a forum did not emerge from the first release?
Here is what you find at their help site:
There is a glossary, which I expected to have to search for the items of interest. But this is all that is available as of now:
I will update with more findings as I have a chance to test them through this weekend. I look forward to hearing from everyone their thoughts on this new Linux OS and maybe help anyone interested in using it futuristically by looking at the system and comparing to other popular distributions.
Sheila